After reading several forums with people arguing about on what routers should we use the “ip pim autorp listener” command, I have decided to write this post explaining things in my own way (of course, with a lot of pictures, as usual). Before starting, just a few words about Auto-RP: it’s a legacy Cisco proprietary method for selecting the RP that uses two functional roles: the Candidate RPs (C-RP) and the Mapping Agent (MA).
Candidate RPs (C-RP):
- routers willing to be RP
- announce themselves to the MA via 224.0.1.39
Mapping Agent (MA):
- decide who will be the RP from the Candidates RP
- will inform the rest of the network about the elected RP via 224.0.1.40
Auto-RP uses in fact a DENSE mode fashion for distributing the announces and discoveries. For this:
- MA must listen for 224.0.1.39
- all multicast speaking routers must listen for 224.0.1.40
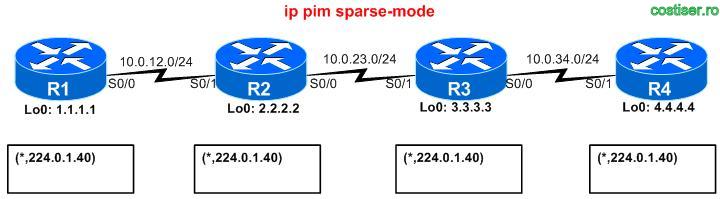
Let’s see how all works. Consider a topology with 4 routers connected in a daisy-chain fashion: R1 <–> R2 <–> R3 <–> R4.
1) configuring “ip pim sparse-mode” on all 4 routers will automatically install a (*,224.0.1.40) on all of them ( at least in IOS 12.4 – not tested in other IOSes !!! )
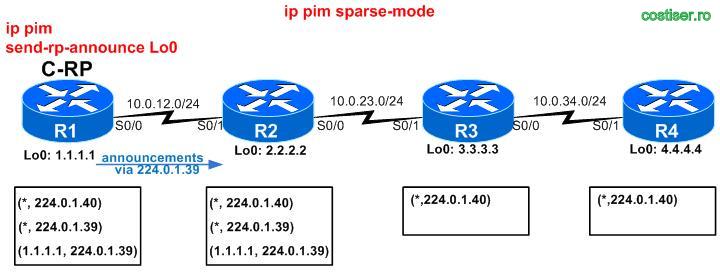
2) configure R1 to be a Candidate-RP (“ip pim send-rp-announce Lo 0“)
=> R1 announce itself as candidate RP via 224.0.1.39 in a DENSE-mode fashion (to all its neighbors):
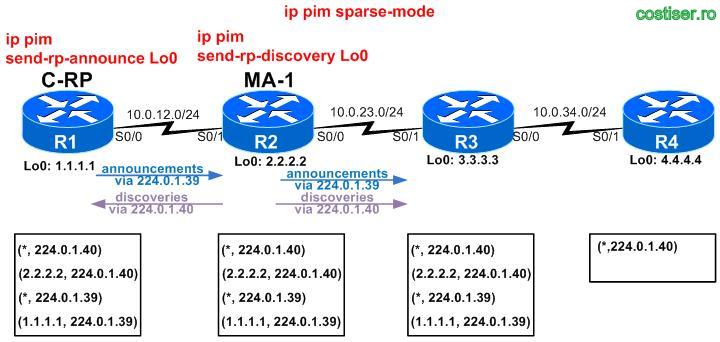
3) configure R2 to be a Mapping Agent (“ip pim send-rp-discovery Lo 0“)
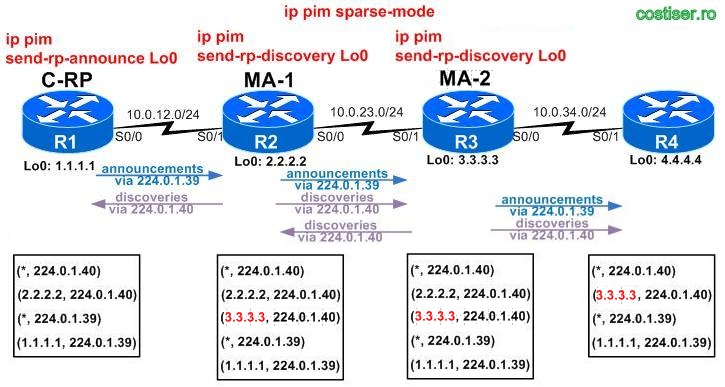
4) configure R3 to be a redundant Mapping Agent (“ip pim send-rp-discovery Lo 0“)
- R1 sees the source of info as being 2.2.2.2 (R2 = MA)
- R2 sees the source of info as being 1.1.1.1 (R1 = C-RP)
- R3 sees the source of info as being 1.1.1.1 (R1 = C-RP)
- R4 sees the source of info as being 3.3.3.3 (R3 = redundant MA)
Another important note: I did not use the “ip pim autorp listener” on any of them !!! I only took advantage of the fact that this command is needed only on routers that are in transit of those groups (routers that need to forward the DENSE information for 224.0.1.39 & 224.0.1.40).